
Top 30 Ethical Hacking Interview Questions and Answers
Mar 18, 2025 5 Min Read 4562 Views
(Last Updated)
The best way to test a defense mechanism is by ethically identifying the vulnerabilities. That is where ethical hacking comes in. Ethical hacking is a dynamic field requiring a solid understanding of both the fundamentals and advanced tactics.
If you’re preparing for an interview, this guide can help you navigate various levels of ethical hacking interview questions and answers, ranging from freshers to advanced ethical hacking roles.
Let us go through some of the best ethical hacking interview questions and answers in this article:
Table of contents
- Top 30 Ethical Hacking Interview Questions and Answers
- Fresher Level Questions
- What is ethical hacking, and how does it differ from malicious hacking?
- Can you explain the five basic stages of ethical hacking?
- What are some common tools used by ethical hackers?
- What is a vulnerability assessment?
- Coding Question: Write a simple Python script to scan for open ports on a specified IP.
- What is the difference between encoding, encryption, and hashing?
- What are white hat, black hat, and gray hat hackers?
- What is a Trojan Horse, and how does it differ from other types of malware?
- What is two-factor authentication, and why is it important in cybersecurity?
- Coding Question: Write a Python function to check if a password meets basic security standards.
- Intermediate Level Questions
- What is the difference between penetration testing and vulnerability assessment?
- Explain the concept of SQL injection and how to prevent it.
- How does Cross-Site Scripting (XSS) work?
- What is a Man-in-the-Middle (MitM) attack?
- Explain the concept of cryptography in cybersecurity.
- Coding Question: Write a script to generate a simple hash for a string in Python.
- What is DNS Spoofing, and how can it be prevented?
- How does ARP Spoofing work, and what is its impact on network security?
- What is a honeypot in cybersecurity?
- Coding Question: Write a Python program to implement a simple brute-force attack on a password-protected zip file.
- Advanced Level Questions
- What are some advanced tactics you would use to bypass a firewall?
- How do you secure a server against DDoS attacks?
- What is an Advanced Persistent Threat (APT)?
- Explain what Buffer Overflow is and how it’s exploited.
- What is zero-day exploitation, and how can organizations protect against it?
- Coding Question: Demonstrate a simple encryption and decryption process in Python using the cryptography library.
- What is the OSI model, and why is it important in cybersecurity?
- Explain the concept of session hijacking and how it can be prevented.
- What is a reverse shell, and when might it be used in ethical hacking?
- Coding Question: Write a Python script that implements a basic Caesar Cipher for encryption and decryption.
- Conclusion
Top 30 Ethical Hacking Interview Questions and Answers

Most people get scared when they appear for an interview. Well, the fear is inevitable but you can gain a lot of self-confidence by preparing the questions and answers.
This section covers some of the best ethical hacking interview questions and answers that can help you crack your dream ethical hacking job!
Fresher Level Questions
1. What is ethical hacking, and how does it differ from malicious hacking?
Ethical hacking involves authorized practices to identify security vulnerabilities in a system, allowing companies to strengthen defenses. Unlike malicious hackers, ethical hackers work legally with consent to protect data and infrastructure.
2. Can you explain the five basic stages of ethical hacking?
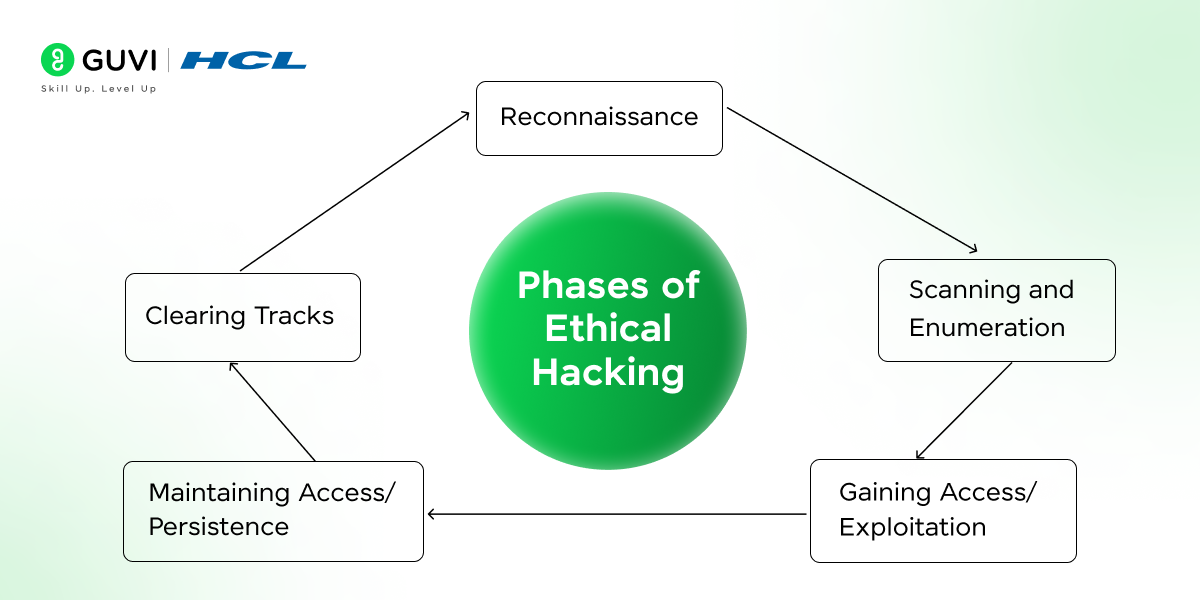
The five basic stages of ethical hacking include:
- Reconnaissance: Gathering information about the target.
- Scanning: Identifying open ports and vulnerabilities.
- Gaining Access: Using exploits to enter the system.
- Maintaining Access: Ensuring continued access if needed.
- Covering Tracks: Removing traces of the hack to prevent detection.
3. What are some common tools used by ethical hackers?
Some popular tools include Nmap (network scanning), Wireshark (packet analysis), Metasploit (exploitation framework), and Burp Suite (web vulnerability scanning).
4. What is a vulnerability assessment?
Vulnerability assessment is the process of scanning and identifying potential vulnerabilities in a system without exploiting them. This helps prioritize security issues for remediation.
5. Coding Question: Write a simple Python script to scan for open ports on a specified IP.
Python
import socket
def scan_ports(ip):
for port in range(1, 1025):
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.settimeout(0.5)
if sock.connect_ex((ip, port)) == 0:
print(f"Port {port} is open.")
sock.close()
scan_ports("127.0.0.1")6. What is the difference between encoding, encryption, and hashing?
Encoding is transforming data into a different format for safe transmission; encryption secures data so only authorized users can decode it, while hashing produces a fixed-length value, or “hash,” that represents the data. Hashing is one-way, while encoding and encryption are reversible with the correct key or method.
7. What are white hat, black hat, and gray hat hackers?
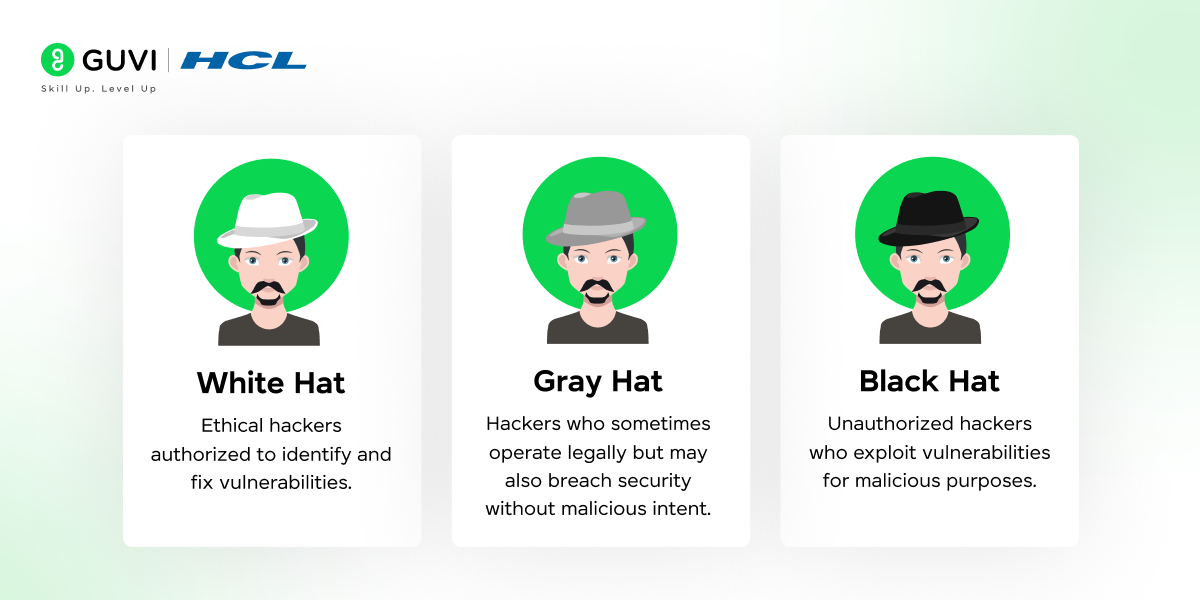
- White Hat: Ethical hackers authorized to identify and fix vulnerabilities.
- Black Hat: Unauthorized hackers who exploit vulnerabilities for malicious purposes.
- Gray Hat: Hackers who sometimes operate legally but may also breach security without malicious intent.
8. What is a Trojan Horse, and how does it differ from other types of malware?
A Trojan Horse is a type of malware disguised as legitimate software. Unlike viruses, which self-replicate, or worms, which spread independently, Trojans rely on users to execute them, allowing attackers to gain unauthorized access or control over the system.
9. What is two-factor authentication, and why is it important in cybersecurity?
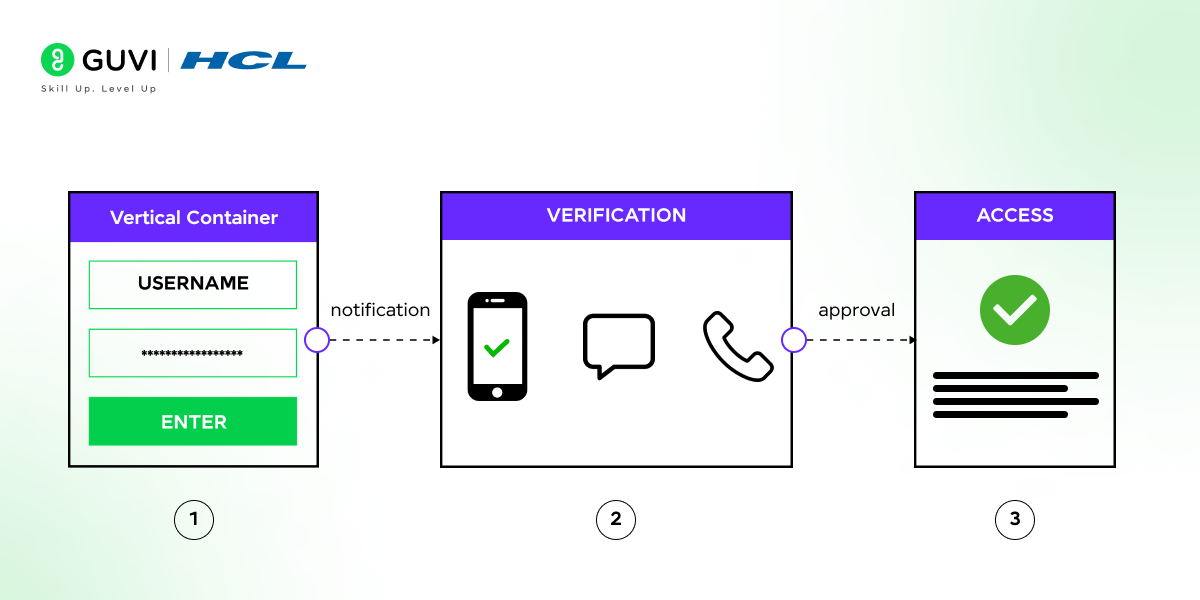
Two-factor authentication (2FA) is a security process that requires two forms of identification. It adds an extra layer of security, making it harder for attackers to access accounts even if they have the password.
10. Coding Question: Write a Python function to check if a password meets basic security standards.
Python
import re
def is_secure_password(password):
if len(password) < 8:
return "Password too short"
if not re.search("[a-z]", password):
return "Password should include lowercase letters"
if not re.search("[A-Z]", password):
return "Password should include uppercase letters"
if not re.search("[0-9]", password):
return "Password should include numbers"
if not re.search("[!@#$%^&*()_+]", password):
return "Password should include special characters"
return "Password is secure"
print(is_secure_password("Ethical123!"))Intermediate Level Questions
11. What is the difference between penetration testing and vulnerability assessment?
Vulnerability assessment is identifying vulnerabilities, while penetration testing is actively exploiting them to determine the extent of the potential damage and to test defenses.
12. Explain the concept of SQL injection and how to prevent it.
SQL injection occurs when attackers insert malicious SQL code into queries, potentially accessing or manipulating data. Preventive measures include using prepared statements, parameterized queries, and sanitizing inputs.
13. How does Cross-Site Scripting (XSS) work?
XSS exploits vulnerabilities in web applications by injecting malicious scripts. This can allow attackers to steal session cookies, redirect users, or deface websites.
14. What is a Man-in-the-Middle (MitM) attack?
In a MitM attack, the attacker intercepts and possibly alters communication between two parties without their knowledge, allowing access to sensitive data. Encryption is a common defense against such attacks.
15. Explain the concept of cryptography in cybersecurity.
Cryptography involves encrypting data to protect it from unauthorized access. It’s fundamental for data security, with techniques like symmetric and asymmetric encryption used for secure communications.
16. Coding Question: Write a script to generate a simple hash for a string in Python.
Python
import hashlib
def generate_hash(text):
result = hashlib.sha256(text.encode())
return result.hexdigest()
print(generate_hash("ethicalhacking"))17. What is DNS Spoofing, and how can it be prevented?
DNS Spoofing, or DNS cache poisoning, is a technique where attackers manipulate DNS records, redirecting users to malicious sites. Prevention methods include DNSSEC (Domain Name System Security Extensions) and using encrypted DNS requests.
18. How does ARP Spoofing work, and what is its impact on network security?
ARP Spoofing involves sending falsified ARP (Address Resolution Protocol) messages to link an attacker’s MAC address to an IP address, redirecting traffic to the attacker’s machine. This can lead to data interception or denial of service. Countermeasures include using static ARP entries and network monitoring.
19. What is a honeypot in cybersecurity?
A honeypot is a decoy system set up to attract attackers, allowing security teams to monitor attack methods and gather intelligence without risking actual systems. Honeypots help improve defense strategies by observing attackers’ techniques in real-time.
20. Coding Question: Write a Python program to implement a simple brute-force attack on a password-protected zip file.
Python
import zipfile
def brute_force_zip(zip_file, password_list):
with zipfile.ZipFile(zip_file, 'r') as zfile:
for password in password_list:
try:
zfile.extractall(pwd=password.encode())
print(f"Password found: {password}")
return True
except:
pass
print("Password not found.")
return False
passwords = ["12345", "password", "secure123"]
brute_force_zip("protected.zip", passwords)Advanced Level Questions
21. What are some advanced tactics you would use to bypass a firewall?
Techniques include IP spoofing, using open ports to avoid blocked ones, encrypting payloads to bypass detection, or tunneling traffic through allowed services like DNS or HTTP.
22. How do you secure a server against DDoS attacks?
Key measures include rate limiting, using anti-DDoS services, implementing WAF (Web Application Firewall), and configuring load balancing to distribute traffic across multiple servers.
23. What is an Advanced Persistent Threat (APT)?
APTs are prolonged, targeted cyber attacks aimed at stealing sensitive information. They often go undetected for long periods, with attackers using advanced techniques to evade detection.
24. Explain what Buffer Overflow is and how it’s exploited.
Buffer Overflow happens when data exceeds memory limits, potentially allowing attackers to inject malicious code. Defense methods include proper validation, using safe functions, and employing ASLR (Address Space Layout Randomization).
25. What is zero-day exploitation, and how can organizations protect against it?
Zero-day refers to an undiscovered vulnerability that hackers exploit before a patch is available. Regular security updates, intrusion detection systems, and monitoring are vital for zero-day defense.
26. Coding Question: Demonstrate a simple encryption and decryption process in Python using the cryptography library.
Python
from cryptography.fernet import Fernet
key = Fernet.generate_key()
cipher = Fernet(key)
text = "SensitiveData".encode()
encrypted = cipher.encrypt(text)
print(f"Encrypted: {encrypted}")
decrypted = cipher.decrypt(encrypted)
print(f"Decrypted: {decrypted.decode()}")27. What is the OSI model, and why is it important in cybersecurity?
The OSI (Open Systems Interconnection) model is a framework that categorizes network functions into seven layers (from Physical to Application). Understanding these layers helps cybersecurity professionals identify where specific security measures should be applied and how attacks might exploit each layer.
28. Explain the concept of session hijacking and how it can be prevented.
Session hijacking occurs when an attacker takes control of a user’s session, typically by stealing a session cookie, allowing unauthorized access. Preventive measures include using secure cookies, implementing SSL/TLS, and monitoring for unusual session activity.
29. What is a reverse shell, and when might it be used in ethical hacking?
A reverse shell allows an attacker to execute commands on a target machine by having the target initiate a connection back to the attacker’s system. Ethical hackers may use reverse shells in penetration tests to gain access to a system and demonstrate its vulnerabilities.
30. Coding Question: Write a Python script that implements a basic Caesar Cipher for encryption and decryption.
Python
def caesar_cipher(text, shift, mode='encrypt'):
result = ""
for char in text:
if char.isalpha():
shift_char = shift if mode == 'encrypt' else -shift
new_char = chr((ord(char) - 65 + shift_char) % 26 + 65) if char.isupper() else chr((ord(char) - 97 + shift_char) % 26 + 97)
result += new_char
else:
result += char
return result
encrypted = caesar_cipher("EthicalHacking", 3, 'encrypt')
print(f"Encrypted: {encrypted}")
print(f"Decrypted: {caesar_cipher(encrypted, 3, 'decrypt')}")If you want to learn more about Ethical Hacking and its best practices, consider enrolling in GUVI’s Ethical Hacking Online Course which teaches everything you need and will also provide an industry-grade certificate!
Conclusion
In conclusion, these questions cover different aspects of ethical hacking, from basic concepts to complex coding challenges.
Preparing for each level will help you develop a well-rounded understanding of ethical hacking and make you more versatile during interviews. Remember, strong fundamentals combined with technical skills can set you apart as an ethical hacker.





























Did you enjoy this article?