
Database Security: 8 Best Practices That You Should Follow
Jan 18, 2025 5 Min Read 5878 Views
(Last Updated)
When you get into the world of technology and software, the database is a must-know aspect irrespective of your domain as it enables you to store all the data that you use and procure.
If you are specialized in the field of data such as a data scientist or a data engineer, then it is mandatory for you to know the best practices for database security. Since you are playing with tonnes of sensitive information, it is only right that you know how to secure those.
If you are just getting started, worry not, this article is for you where we will cover everything about database security starting from its very definition to the best practices. So, all you need to do is, sit tight and read till the end.
Let us get started!
Table of contents
- What is Database Security?
- Why is Database Security Essential?
- Protecting Sensitive Information
- Ensuring Data Integrity
- Compliance with Regulations
- Preventing Financial Loss
- Safeguarding Business Continuity
- Mitigating Cybersecurity Threats
- Protecting Reputation and Brand
- Database Security: Best Practices
- Implement Strong Access Controls
- Use Strong Authentication Mechanisms
- Encrypt Data
- Regularly Update and Patch Systems
- Implement Robust Backup and Recovery Procedures
- Monitor and Audit Database Activity
- Educate and Train Employees
- Apply Network Security Measures
- Conclusion
- FAQs
- How does encryption enhance database security?
- Why is it important to have a strong password policy for database access?
- How does role-based access control (RBAC) differ from discretionary access control (DAC)?
- Why is it important to test backup and recovery procedures regularly?
- What is a SQL injection attack and how can it be prevented?
What is Database Security?
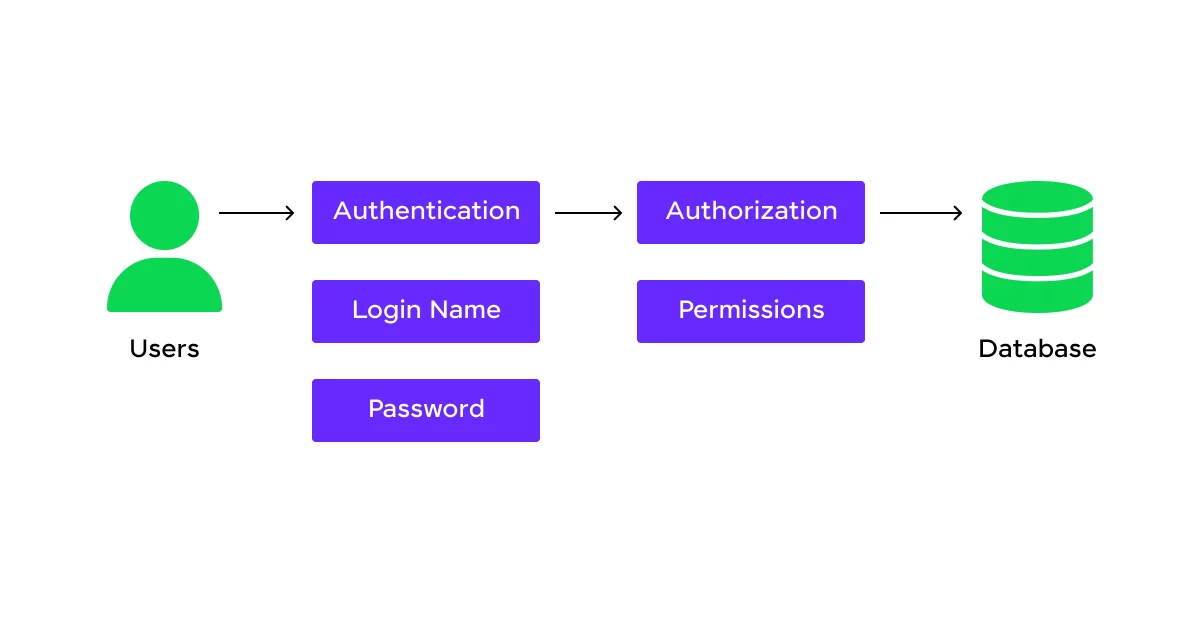
As mentioned earlier, let us start with the basics, a ground-level knowledge of what database security truly is.
In database management systems, database security refers to the various measures and practices used to protect a database from unauthorized access, misuse, and breaches.
It involves ensuring that only authorized users can access the data, keeping the information safe from hackers or malicious activities, and maintaining the integrity and accuracy of the data.
This protection is vital for keeping personal information, business secrets, and other sensitive data safe, which helps in maintaining trust, complying with legal requirements, and preventing financial losses. In simple terms, database security is like having strong locks and guards for your digital data storage.
Read More: A Comprehensive Guide on DBMS Trends
Why is Database Security Essential?
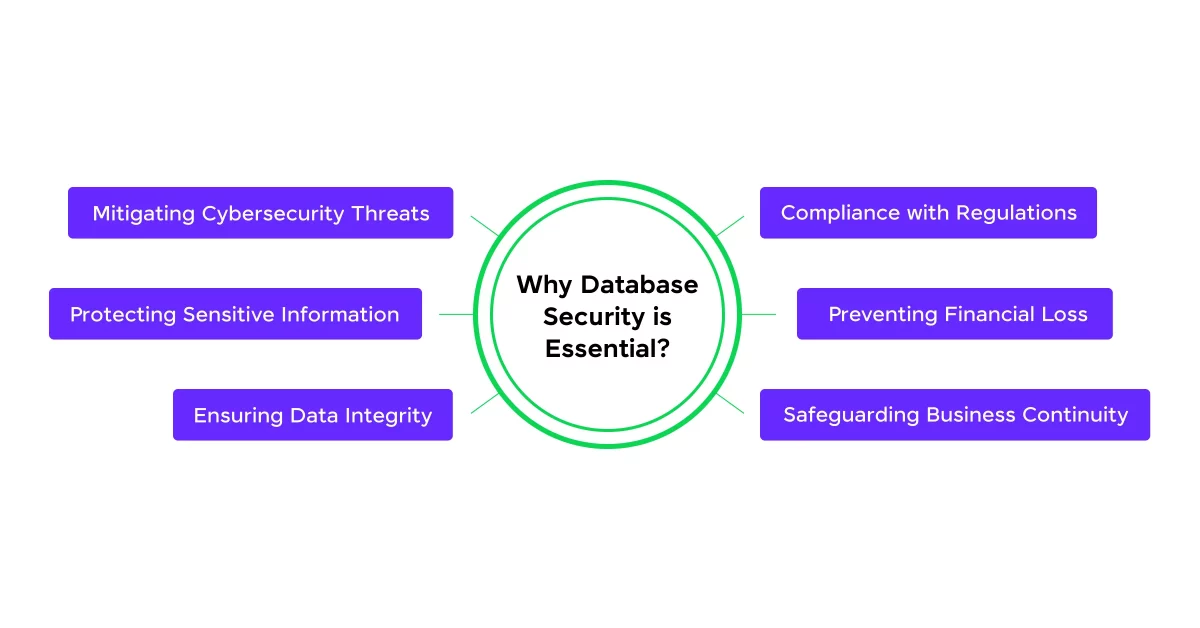
Database security is not just a technical concern; it’s a fundamental aspect of maintaining the trust, integrity, and functionality of any organization that relies on data.
But before we go any further, you must have a basic understanding of data science. If not, consider enrolling in a professionally certified online Data Science Course that teaches you everything about databases and helps you get started as a data scientist.
Additionally, if you want to explore SQL through a self-paced course, try GUVI’s SQL Server course.
Understanding why database security is essential can help you prioritize and implement effective measures to protect your data.
1. Protecting Sensitive Information
Databases often contain sensitive information, including personal data, financial records, and proprietary business details. Securing this data is crucial for several reasons:
- Preventing Identity Theft: Personal information, such as social security numbers, addresses, and credit card details, must be safeguarded to prevent identity theft and financial fraud.
- Protecting Intellectual Property: Proprietary business information and trade secrets need to be secure to maintain a competitive edge and protect innovation.
2. Ensuring Data Integrity
Data integrity refers to the accuracy and consistency of data stored in a database. Here’s why it’s vital:
- Reliable Decision-Making: Businesses rely on accurate data to make informed decisions. Compromised data can lead to poor decision-making and strategic missteps.
- Maintaining Trust: Customers and partners need to trust that the information they provide will remain accurate and unchanged. Data breaches or corruption can erode this trust and damage relationships.
3. Compliance with Regulations
Various laws and regulations mandate the protection of certain types of data. Ensuring database security helps in:
- Avoiding Penalties: Non-compliance with regulations such as GDPR, HIPAA, or CCPA can result in hefty fines and legal consequences.
- Meeting Industry Standards: Adhering to industry-specific standards, such as PCI DSS for payment data, helps maintain compliance and avoid potential penalties.
Also Read: Revolutionizing Data Handling: Big Data Management with DBMS Dissected
4. Preventing Financial Loss
The financial impact of a data breach can be substantial, affecting an organization’s bottom line in several ways:
- Direct Costs: These include expenses related to breach response, legal fees, and compensations.
- Indirect Costs: Long-term financial impacts such as loss of business, brand damage, and decreased customer loyalty can be even more significant.
5. Safeguarding Business Continuity
Database security plays a crucial role in ensuring business continuity and resilience:
- Minimizing Downtime: Effective security measures can prevent attacks that lead to system downtime, ensuring continuous business operations.
- Disaster Recovery: Robust security practices include backup and recovery solutions that help organizations quickly restore operations after an incident.
6. Mitigating Cybersecurity Threats
The cybersecurity landscape is constantly evolving, with new threats emerging regularly. Database security helps in:
- Preventing Unauthorized Access: Measures like strong authentication and access controls prevent unauthorized users from accessing sensitive data.
- Detecting and Responding to Threats: Continuous monitoring and auditing help detect suspicious activities early, allowing for prompt response to mitigate potential breaches.
7. Protecting Reputation and Brand
An organization’s reputation can be severely damaged by a data breach:
- Maintaining Customer Trust: Customers expect their data to be handled securely. A breach can lead to a loss of trust and customer churn.
- Upholding Brand Image: Repeated or high-profile security incidents can tarnish a brand’s image, making it difficult to attract and retain customers.
Database security is essential for protecting sensitive information, ensuring data integrity, complying with regulations, preventing financial loss, safeguarding business continuity, mitigating cybersecurity threats, and protecting an organization’s reputation.
Learn More: Types of DBMS: Relational vs. Non-Relational Databases
Database Security: Best Practices
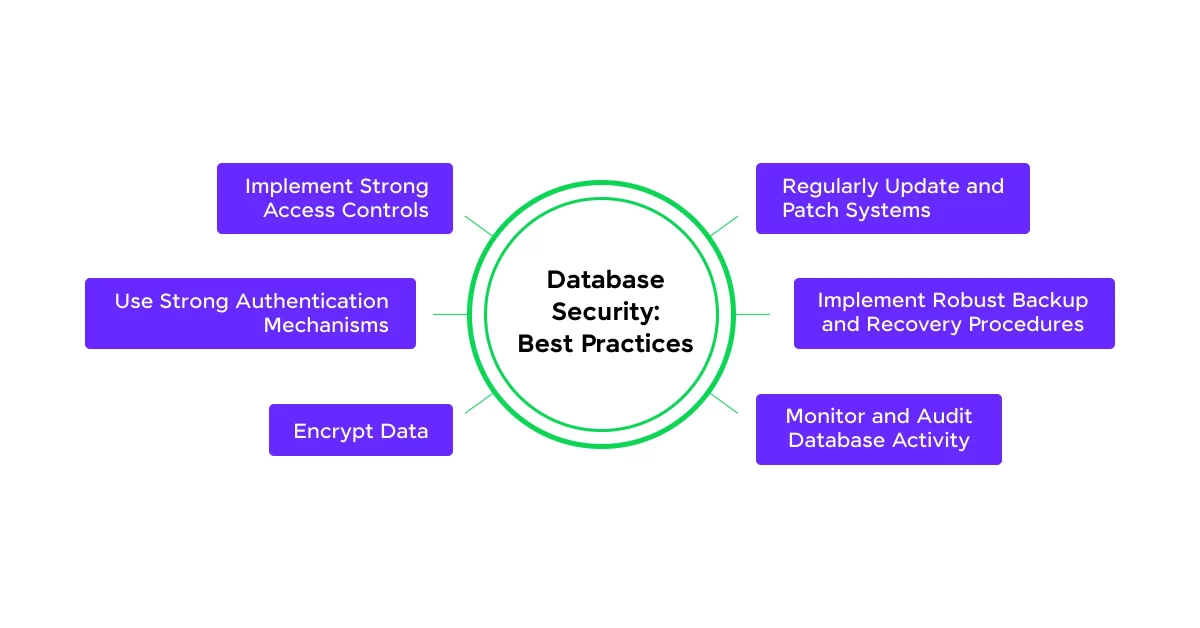
Now that you understand what database security is and why it is essential for you to keep it in mind, let us now jump to the topic of the day, best practices for database security.
Data is one of the most valuable assets for any organization. Ensuring its security is very important to maintain trust and comply with various regulations. Let us see some of the best practices to secure our personal and sensitive data:
1. Implement Strong Access Controls
Access control is the first line of defense in database security. Here’s how you can implement it effectively:
- Principle of Least Privilege (PoLP): Only grant users the minimum access necessary to perform their tasks. This reduces the risk of accidental or malicious data manipulation.
- Role-Based Access Control (RBAC): Assign permissions based on roles rather than individual users. This simplifies management and ensures consistent access policies.
- Regular Audits: Periodically review access permissions to ensure they align with current roles and responsibilities.
2. Use Strong Authentication Mechanisms
Ensuring that only authorized users can access your database is crucial. Employ the following authentication measures:
- Multi-Factor Authentication (MFA): Adding an extra layer of security, such as a one-time password (OTP) or biometric verification, can significantly enhance security.
- Secure Password Policies: Enforce strong password policies, including complexity requirements and regular updates. Educate users on the importance of not reusing passwords.
3. Encrypt Data
Encryption is a powerful tool for protecting sensitive data both at rest and in transit:
- Data at Rest: Use encryption methods like AES (Advanced Encryption Standard) to secure stored data. Ensure encryption keys are managed securely.
- Data in Transit: Encrypt data being transmitted over networks using protocols like TLS (Transport Layer Security) to prevent interception by unauthorized parties.
Also Read: Mastering Database Optimization: Advanced Indexing Techniques for Performance
4. Regularly Update and Patch Systems
Outdated software can have vulnerabilities that attackers can exploit. Follow these guidelines to keep your systems secure:
- Automatic Updates: Enable automatic updates for your database software and underlying operating systems.
- Patch Management: Establish a robust patch management process to apply updates promptly and efficiently. Regularly monitor for new patches and vulnerabilities.
5. Implement Robust Backup and Recovery Procedures
Despite best efforts, breaches or data loss can still occur. Having a solid backup and recovery strategy ensures you can restore your data with minimal downtime:
- Regular Backups: Schedule regular backups and store them securely, both onsite and offsite.
- Test Restores: Periodically test your backup restoration process to ensure it works as expected and that data can be recovered quickly.
6. Monitor and Audit Database Activity
Continuous monitoring and auditing can help detect and respond to suspicious activities before they become significant issues:
- Database Activity Monitoring (DAM): Implement DAM tools to track database access and activities in real time. Look for abnormal patterns that might indicate a breach.
- Audit Logs: Maintain comprehensive audit logs that record all access and changes to the database. Regularly review these logs for any anomalies.
7. Educate and Train Employees
Human error is a common cause of security breaches. Regular training and awareness programs can help mitigate this risk:
- Security Awareness Training: Conduct regular training sessions to educate employees on best security practices, including phishing awareness and data handling protocols.
- Incident Response Drills: Perform drills to ensure employees know how to respond to security incidents promptly and effectively.
8. Apply Network Security Measures
Protecting the network environment where your database resides is equally important:
- Firewalls: Configure firewalls to restrict access to the database server only to authorized IP addresses.
- Intrusion Detection and Prevention Systems (IDPS): Deploy IDPS to detect and prevent malicious activities within your network.
By implementing these best practices, you can significantly reduce the risk of data breaches and ensure the integrity and confidentiality of your data.
Explore: Data Warehousing: Concepts and Implementation for Data Management
If you want to learn more about Database security practices in data science, then consider enrolling in GUVI’s Certified Data Science Course which not only gives you theoretical knowledge but also practical knowledge with the help of real-world projects.
Alternatively, if you would like to explore SQL through a Self-paced course, try
GUVI’s SQL Server certification course.
Conclusion
In conclusion, securing your database is a continuous process that requires vigilance, regular updates, and a proactive approach. Remember, the goal is to build a dynamic security framework that adapts to evolving threats and keeps your database secure.
By following these guidelines, you’ll be well on your way to establishing a secure database environment that protects your organization’s valuable data assets. If you have any questions or need further assistance, feel free to reach out.
Also, Find Out the 10 Best Database Management Systems For Software Developers
FAQs
Encryption transforms readable data into an unreadable format, ensuring that even if data is intercepted, it cannot be understood without the decryption key.
A strong password policy ensures that passwords are difficult to guess or crack, reducing the likelihood of unauthorized access.
RBAC assigns permissions based on user roles, while DAC allows data owners to control access based on user identities.
Regular testing ensures that backups are reliable and can be restored quickly in case of data loss or a security incident, minimizing downtime and data loss.
SQL injection is an attack where malicious SQL code is inserted into a query to manipulate the database. It can be prevented by using parameterized queries and input validation.





















![Mastering Database Optimization: Advanced Indexing Techniques for Performance [2025] 6 Feature Image - Mastering Database Optimization Advanced Indexing Techniques for Performance](https://www.guvi.in/blog/wp-content/uploads/2024/04/Feature-Image-Mastering-Database-Optimization-Advanced-Indexing-Techniques-for-Performance.webp)







Did you enjoy this article?