
30 Sure Shot Cybersecurity Interview Questions And Answers
Jun 09, 2025 5 Min Read 7425 Views
(Last Updated)
Since the world is going full digital now, the security of those technologies is of paramount importance. That’s why the field of cybersecurity is at an all-time high!
In order to crack this in-demand role, you need to be well-prepared with the cybersecurity interview questions and answers!
If you don’t know where to start, here’s a guide to help you tackle cybersecurity interview questions and answers that might come your way. Whether you’re a fresher, an intermediate-level professional, or aiming for an advanced role, these questions are designed to cover key concepts in cybersecurity.
Table of contents
- Cybersecurity Interview Questions And Answers
- Level 1: Fresher-Level Questions
- What is Cybersecurity, and why is it important?
- Can you explain the difference between a virus, a worm, and a Trojan?
- What is a firewall, and how does it work?
- What is Two-Factor Authentication (2FA), and how does it enhance security?
- Can you explain the CIA Triad in cybersecurity?
- Level 2: Intermediate-Level Questions
- What is the difference between symmetric and asymmetric encryption?
- What is a Man-in-the-Middle (MitM) attack? How would you prevent it?
- Can you explain the concept of “least privilege” in access control?
- Describe SQL Injection and how you can prevent it.
- How would you handle a DDoS (Distributed Denial of Service) attack?
- Write a basic Python script to check for open ports on a target IP address.
- Describe the process of penetration testing and its phases.
- What is Cross-Site Scripting (XSS), and how can you prevent it?
- Can you explain what a sandbox is in cybersecurity?
- Explain SSL/TLS and how they secure data transmission.
- Level 3: Advanced-Level Questions
- What is Zero Trust architecture, and why is it important?
- How does a Public Key Infrastructure (PKI) work in securing communications?
- Explain the concept of lateral movement in cybersecurity.
- Describe DNS Tunneling and its impact on cybersecurity.
- What is the OWASP Top 10, and why is it important?
- Can you write a Python script to detect a brute-force login attempt?
- Explain the use of SIEM (Security Information and Event Management) systems.
- Describe the process of risk assessment in cybersecurity.
- What is Endpoint Detection and Response (EDR)?
- What is Phishing, and how can you prevent it?
- Explain what a VPN (Virtual Private Network) is and its role in cybersecurity.
- What is a digital certificate?
- How would you approach setting up a security strategy for a large organization?
- What is a honeypot, and how is it used in cybersecurity?
- Write a Python script to generate an MD5 hash of a file.
- Conclusion
Cybersecurity Interview Questions And Answers

To ease up your learning process, we have made sure to segregate the questions under 3 categories: fresher-level questions, Intermediate questions, and Advanced questions.
Level 1: Fresher-Level Questions
These Cybersecurity interview questions are Ideal for beginners and fresh graduates, These questions focus on cybersecurity basics, terminology, and foundational concepts.
1. What is Cybersecurity, and why is it important?
Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. Cybersecurity is essential because it safeguards sensitive information, prevents unauthorized access, and protects against data breaches, which can have severe consequences for organizations and individuals alike.
2. Can you explain the difference between a virus, a worm, and a Trojan?
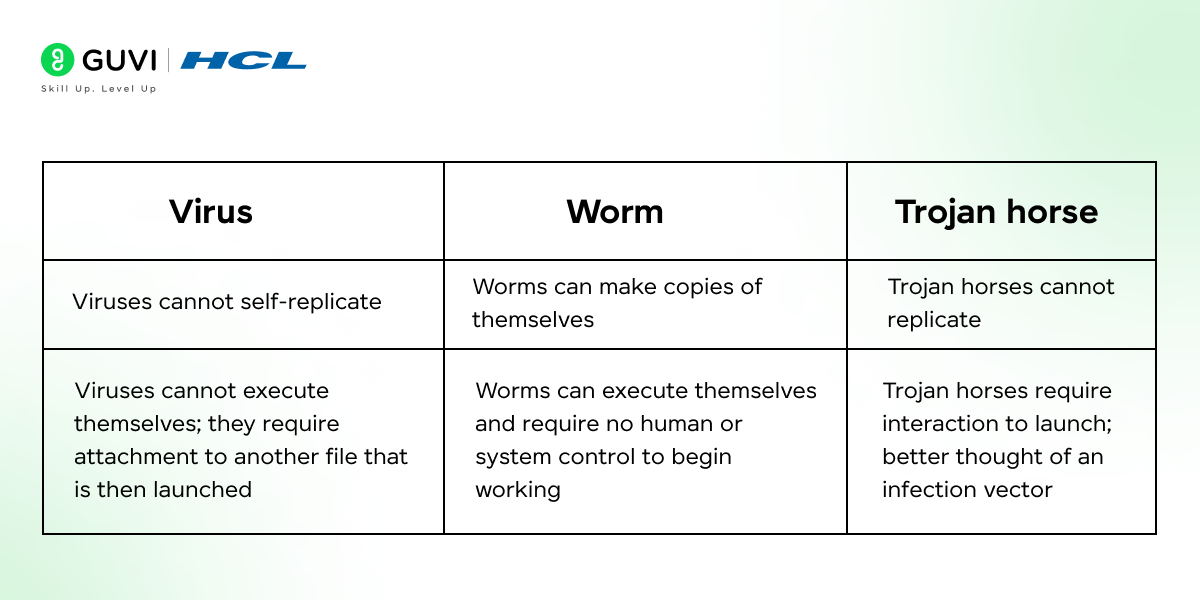
- Virus: A malicious code that attaches itself to a host program, spreading only when the host program runs.
- Worm: A standalone malware that replicates itself to spread to other systems without user intervention.
- Trojan: A disguised malware that tricks users into installing it, often masquerading as legitimate software.
3. What is a firewall, and how does it work?
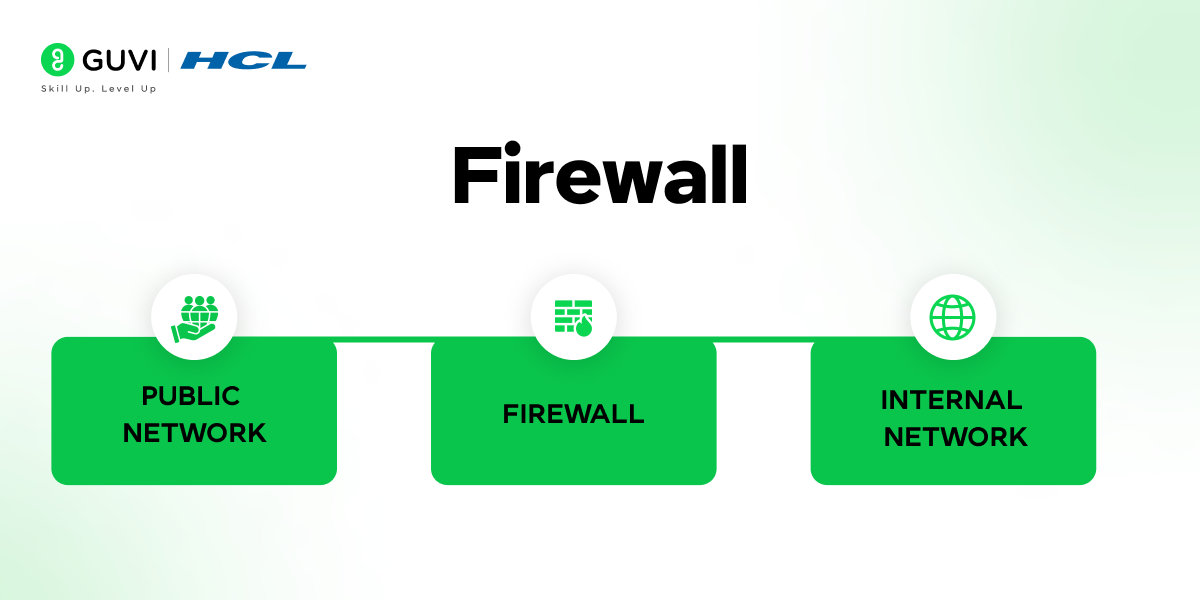
A firewall is a network security device that monitors and filters incoming and outgoing network traffic. It works by establishing a barrier between a trusted internal network and an untrusted external network, using rules to decide whether to allow or block specific traffic.
4. What is Two-Factor Authentication (2FA), and how does it enhance security?
Two-Factor Authentication adds a layer of security by requiring users to provide two types of information to verify their identity, typically something they know (password) and something they have (e.g., OTP on phone). This reduces the risk of unauthorized access.
5. Can you explain the CIA Triad in cybersecurity?
The CIA Triad stands for Confidentiality, Integrity, and Availability:
- Confidentiality ensures sensitive information is accessible only to authorized individuals.
- Integrity ensures the accuracy and trustworthiness of data.
- Availability ensures that authorized users have access to information and resources when needed.
Level 2: Intermediate-Level Questions
For those with some experience, these questions delve deeper into cybersecurity practices, methodologies, and real-world application scenarios.
6. What is the difference between symmetric and asymmetric encryption?
- Symmetric encryption uses the same key for both encryption and decryption, making it faster but less secure in key distribution.
- Asymmetric encryption uses a pair of keys (public and private), enhancing security by not requiring the key to be shared.
7. What is a Man-in-the-Middle (MitM) attack? How would you prevent it?
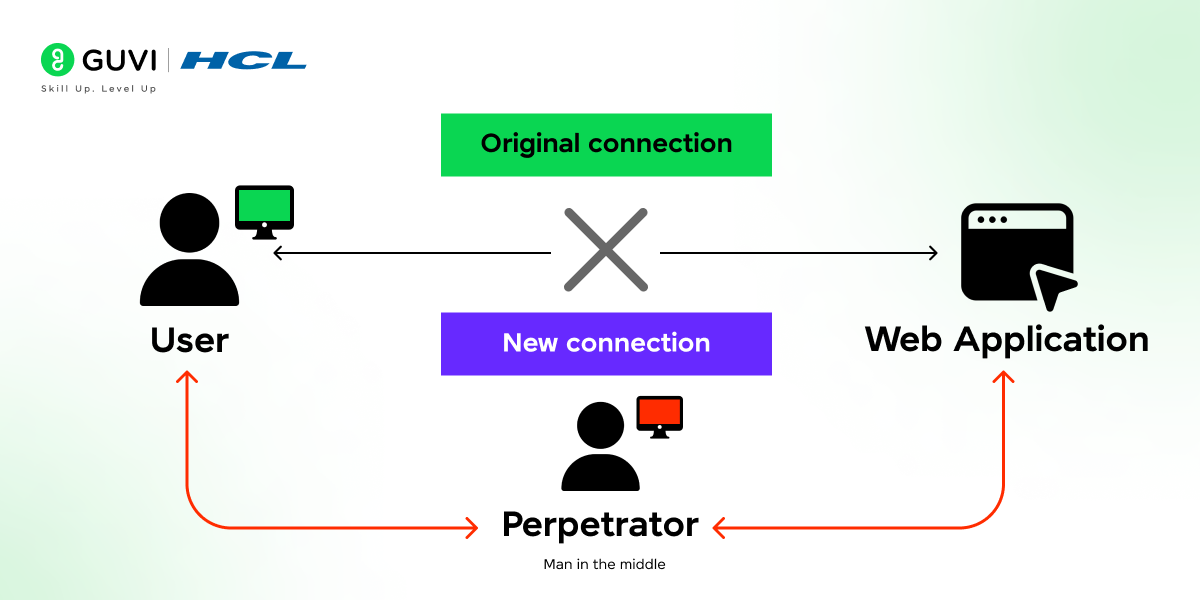
A MitM attack occurs when an attacker intercepts and potentially alters the communication between two parties. Preventive measures include using encryption (HTTPS), VPNs, and strong authentication methods to secure communications.
8. Can you explain the concept of “least privilege” in access control?
The principle of least privilege restricts user access to only the information and resources necessary for their role. It minimizes potential security risks by limiting exposure in case of compromised accounts.
9. Describe SQL Injection and how you can prevent it.
SQL Injection is a code injection technique that manipulates SQL queries, allowing attackers to execute malicious SQL statements. Prevent it by using parameterized queries, input validation, and prepared statements.
10. How would you handle a DDoS (Distributed Denial of Service) attack?
Handling a DDoS attack includes:
- Monitoring traffic patterns to identify unusual spikes.
- Implementing rate limiting to restrict excessive requests.
- Using DDoS protection tools such as Cloudflare or AWS Shield.
- Isolating the attacked server to contain the impact.
11. Write a basic Python script to check for open ports on a target IP address.
Python
import socket
def check_open_ports(ip, ports):
open_ports = []
for port in ports:
sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
sock.settimeout(1)
result = sock.connect_ex((ip, port))
if result == 0:
open_ports.append(port)
sock.close()
return open_ports
ip = '192.168.1.1'
ports = [22, 80, 443]
print(f"Open ports: {check_open_ports(ip, ports)}")12. Describe the process of penetration testing and its phases.
Penetration testing is a method to identify vulnerabilities by simulating cyberattacks. It consists of five phases: Planning, Reconnaissance, Scanning, Exploitation, and Reporting. Each phase is essential to assess and improve the security of a system.
13. What is Cross-Site Scripting (XSS), and how can you prevent it?
XSS is an injection attack where malicious scripts are injected into websites to execute on the user’s browser. Prevention includes input validation, encoding outputs, and using Content Security Policies (CSP).
14. Can you explain what a sandbox is in cybersecurity?
A sandbox is an isolated environment used to run suspicious files or applications securely without affecting the host system. It’s used to analyze and detect malware behavior without risking the organization’s network.
15. Explain SSL/TLS and how they secure data transmission.
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are protocols that encrypt data transmitted between a client and a server, ensuring data integrity and security. They prevent interception and tampering, protecting sensitive information during transfer.
Level 3: Advanced-Level Questions
These questions are for experienced professionals looking to demonstrate their in-depth technical knowledge and problem-solving skills in cybersecurity.
16. What is Zero Trust architecture, and why is it important?
Zero Trust is a security model that requires strict identity verification for every user or device trying to access resources on a private network, regardless of location. It’s crucial for preventing unauthorized access and protecting against lateral movement within networks.
17. How does a Public Key Infrastructure (PKI) work in securing communications?
PKI secures communications by managing digital certificates and public-key encryption. It enables secure data transmission by verifying the identity of devices and individuals, using certificate authorities (CAs) and digital signatures.
18. Explain the concept of lateral movement in cybersecurity.
Lateral movement is a tactic used by attackers to move deeper into a network once they have gained initial access. They explore the network to escalate privileges and reach sensitive data or critical systems.
19. Describe DNS Tunneling and its impact on cybersecurity.
DNS Tunneling is a technique used to send HTTP and other protocol traffic over DNS, which can bypass security controls. It can be used for malicious activities, such as data exfiltration, as DNS traffic often goes unmonitored.
20. What is the OWASP Top 10, and why is it important?
The OWASP Top 10 is a list of the most critical security risks for web applications, published by the Open Web Application Security Project. It’s an industry standard that helps developers and security professionals focus on preventing the most common vulnerabilities.
21. Can you write a Python script to detect a brute-force login attempt?
Python
from collections import defaultdict
from datetime import datetime, timedelta
def detect_brute_force(logins, time_limit=timedelta(minutes=5), threshold=5):
attempts = defaultdict(list)
brute_force_ips = set()
for ip, timestamp in logins:
attempts[ip].append(timestamp)
recent_attempts = [t for t in attempts[ip] if t > timestamp - time_limit]
if len(recent_attempts) >= threshold:
brute_force_ips.add(ip)
return brute_force_ips
logins = [('192.168.1.1', datetime.now() - timedelta(minutes=i)) for i in range(6)]
print(f"Brute-force detected from IPs: {detect_brute_force(logins)}")22. Explain the use of SIEM (Security Information and Event Management) systems.
SIEM systems aggregate and analyze security data from across the organization. They help detect and respond to potential threats in real-time by collecting logs, correlating events, and alerting security teams to suspicious activity.
23. Describe the process of risk assessment in cybersecurity.
Risk assessment involves identifying assets, evaluating vulnerabilities and threats, determining potential impacts, and prioritizing risks. It helps organizations focus on high-risk areas to implement effective security measures.
24. What is Endpoint Detection and Response (EDR)?
EDR solutions monitor and respond to suspicious activities on endpoints (e.g., laptops, servers). They provide real-time insights into malicious behavior and facilitate quick containment and response to potential threats.
25. What is Phishing, and how can you prevent it?
Phishing is a social engineering attack where attackers impersonate a legitimate entity to trick individuals into providing sensitive information. Prevention methods include educating users, using email filters, and implementing multi-factor authentication.
26. Explain what a VPN (Virtual Private Network) is and its role in cybersecurity.
A VPN is a tool that creates a secure, encrypted connection over the internet, allowing users to safely access a private network. It is commonly used to protect data and maintain privacy, especially when using public Wi-Fi.
27. What is a digital certificate?
A digital certificate is an electronic document that verifies the identity of an individual, organization, or device. It uses encryption to secure and authenticate information exchanged over the internet, playing a crucial role in secure communications.
28. How would you approach setting up a security strategy for a large organization?
Start by conducting a risk assessment to identify critical assets, threats, and vulnerabilities. Develop a layered defense strategy covering network security, data encryption, access control, incident response plans, and regular security audits. Involve continuous monitoring, employee training, and compliance with regulatory standards.
29. What is a honeypot, and how is it used in cybersecurity?
A honeypot is a decoy system or server designed to attract attackers and study their behavior. By analyzing how attackers interact with the honeypot, organizations can identify and understand potential threats, improving their defenses.
30. Write a Python script to generate an MD5 hash of a file.
Python
import hashlib
def generate_md5(file_path):
hash_md5 = hashlib.md5()
with open(file_path, "rb") as f:
for chunk in iter(lambda: f.read(4096), b""):
hash_md5.update(chunk)
return hash_md5.hexdigest()
file_path = 'example.txt'
print(f"MD5 hash of the file: {generate_md5(file_path)}")If you want to learn more about Cybersecurity and its best practices, consider enrolling in GUVI’s Cybersecurity Online Course, which teaches everything you need and will also provide an industry-grade certificate!
Conclusion
In conclusion, with these 30 questions covering freshers, intermediate, and advanced levels, you’re well-prepared to tackle cybersecurity interviews confidently. Focus on understanding these concepts deeply, as cybersecurity is a dynamic field where knowledge is constantly evolving. Best of luck in your preparation journey!






















![How to Become a Security Architect: A Beginner's Guide [2025] 7 security architect](https://www.guvi.in/blog/wp-content/uploads/2025/05/How-to-Become-a-Systems-Engineer_-Expert-Guide-for-Beginners.png)





Did you enjoy this article?