
8 Different Types of Cybersecurity and Threats Involved
Apr 16, 2025 4 Min Read 6549 Views
(Last Updated)
Cybersecurity refers to the protection of devices, processes, infrastructure, and assets of the organization from cyberattacks, data theft, breaches, unauthorized access, etc. With the advent of technology and the increasing interconnectedness of organizational systems and networks, effective cybersecurity management and strategy are necessary for organizations of all sizes and types accordingly. Investments are flowing into this field and the market is projected to be a staggering 403 billion US dollars by 2027. This in turn has led to a spurt in demand for experts in the field of cyber security. Cybersecurity is an umbrella term that encompasses different types of security. In this article, we’re trying to deconstruct various types of cybersecurity. So let’s dig in.
Table of contents
- Application Security
- Information security
- Now let's look at the need for Information Security
- Disaster Recovery
- Network Security
- Common Examples of Network Security Implementation
- Website Security
- Endpoint Security
- Cloud Security
- Internet of Things
- Different threats in IoT security.
- Summing up the list of types of cybersecurity
Application Security
Application security constitutes the measures and countermeasures meant to tackle threats and vulnerabilities that arise in the development stage of an application such as design application, development, deployment, maintenance, upgrade, etc. It mainly refers to the measure implemented in order to prevent the app’s code or data from being stolen or hijacked.
There are various hardware, software, and procedures deployed to detect as well as mitigate security flaws in the application development process. Since 2007, OWASP (The Open Web Application Security Project ) has tracked and classified 10 critical threats to web application development, such as injection, broken authentication, cross-site scripting, misconfiguration, and more.
Some of the techniques to mitigate these attacks include input parameters, validation sessions, management, user authentication, and authorization, etc. Application security also prevents bot attacks and ensures to it stops any malicious interaction with the application and its APIs. The ultimate goal is to make sure that apps remain protected even as DevOps releases new content.
Information security
Information security refers to the protection of information and data from theft, unauthorized access, breaches, etc., primarily to uphold user privacy and prevent identity theft. Information security is evolving as one of the major requirements in businesses worldwide today.
Data is one of the major assets of the Digital Economy, so naturally, the protection of data is very, very important. Starting from big corporate companies to small startups, all have started investing in information security.
There are three basic principles of information security, also referred to as the CIA.
- Confidentiality
- Integrity
- Availability
Confidentiality ensures that sensitive information is not accessed by unauthorized parties. Integrity ensures that the information is not modified by accident or compromised for any reason. If it is modified by accident, it should be recovered at any cost. The third one availability, ensures that the information is highly available on a regular basis. Businesses prefer & rely on the high availability of information always.

Now let’s look at the need for Information Security
- Protect the functionality of the organization: Every organization has a set of policies to follow, and every employee needs to abide by these rules and function in the organization.
- Ensure the safe operation of the application: Every organization has various applications. These applications need to be secured safely, so the organization needs to create a safe environment to handle these applications.
- Protect the data collected by the organization. Companies collect various data from different clients. All this data is very confidential, so protecting this data is very important
Disaster Recovery
Disaster recovery involves planning and strategizing to enable organizations to recover from cybersecurity / IT disasters. The type of cybersecurity includes risk assessment, analysis, prioritizing, and establishing disaster response and recovery mechanisms in place. This enables organizations to recover faster from disasters and minimize losses.
Network Security
Network security is a broad concept encompassing a wide range of technologies, processes, and devices. In simple terms, it constitutes monitoring and preventing authorized access and exploitation of the internal networks of an organization by leveraging both hardware and software technologies. Today’s network environment is complex, with a constantly changing threat environment and hackers looking to expose vulnerabilities. This is one of the biggest types of cybersecurity that offers great job opportunities across all sectors and organizations.
These vulnerabilities and flaws can exist in various forms such as data, devices, users, applications, and location. As a result many organizations now implement security management tools and applications to combat these threats, exploits, and regulatory noncompliance. These safety nets are eminent when a few minutes of downtime can lead to widespread disruption and massive damage to an organization’s operations and revenues.
There are various layers It ensures that internal networks are safe reliable and usable antivirus and anti-spyware software, VPN, IPS, firewall, etc. are used to prevent cyber threats from facing the organization.
Common Examples of Network Security Implementation
- New passwords
- Extra Login
- Antivirus Program
- Antispyware Software
- Monitored Internet Access
- Firewalls
- Encryption
Website Security
Just like the name suggests, Website security is used to prevent and protect websites from cybersecurity risks on the Internet. The holistic website security programs will cover the websites, databases, applications, source codes, and files. There has been a steady rise in the number of data breaches on websites in the past few years , resulting in identity theft, downtime, financial losses, loss of reputation and brand image, etc.
The main reason for this has been the misconception among website owners that their website is protected by a website hosting provider, thus leaving them vulnerable to cyber-attacks.
5 biggest Cybersecurity Certifications to advance your career in an evergrowing Cybersecurity Niche
Endpoint Security
Endpoint security enables organizations to protect their servers, workstations, and mobile devices from remote and local cyber attacks since devices on a network are interconnected. Primarily used to assess all the entry points for threats and vulnerabilities. It effectively secures the network by blocking all the attempts made to access these entry points via monitoring, file integrity, antivirus and anti-malware software, etc.
Also known as the zero-trust security model, endpoint security believes in creating micro-segments around data wherever it may be. By implementing endpoint security, companies can secure end-user services such as laptops and desktops with network and data security controls. They can also advance their threat protection using anti-ransomware and anti-phishing.
Cloud Security
Now, Cloud Security is a subset of cybersecurity that focuses on ensuring protection for cloud computing systems. It includes maintaining Security and data privacy online spanning applications, infrastructure, and platforms. Cloud providers like AWS or AZURE work together with their clientele, whether individuals, from SMEs to big enterprises to prevent the attack by exposing cloud vulnerabilities.
As organizations rapidly transition to cloud computing, securing the cloud becomes a major priority for companies. An adequate cloud security strategy includes cybersecurity solutions, policies, controls, and services that assist in preserving an organization’s entire cloud deployment. ( Data, Application, infrastructure, etc) against attacks.
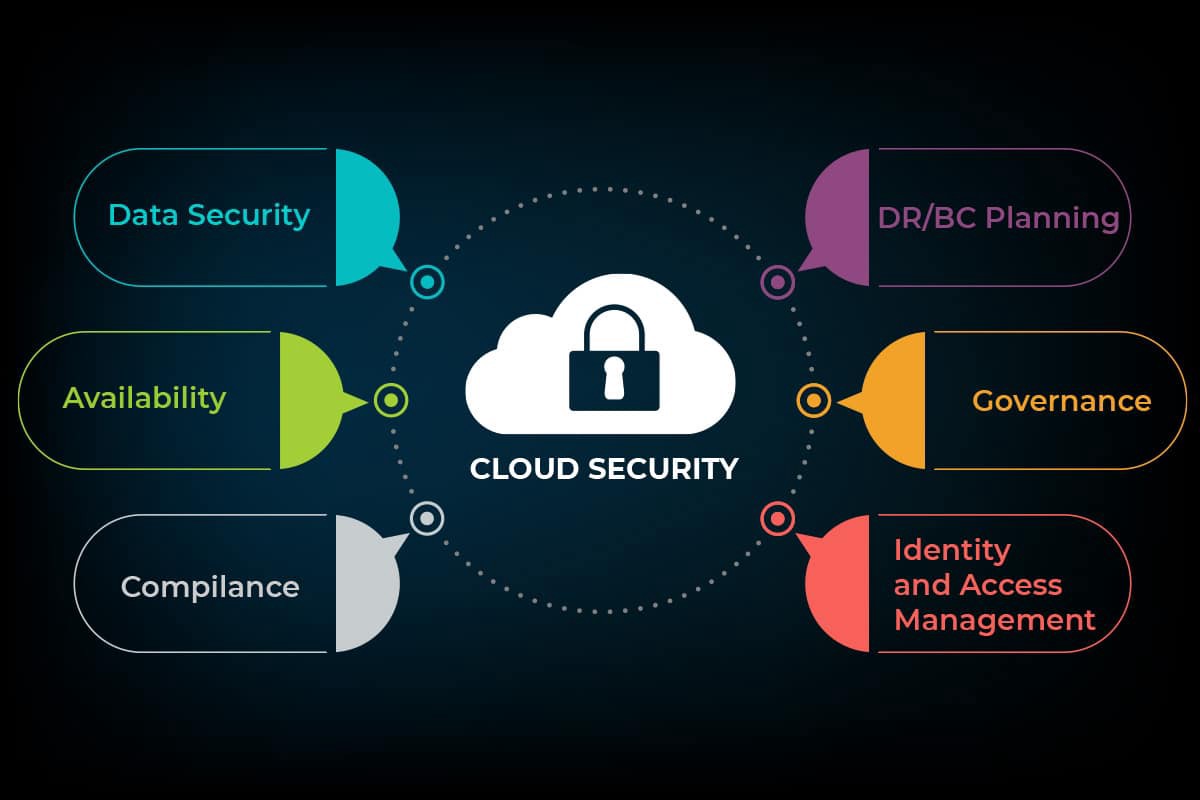
While most of the cloud hosting companies offer security solutions, they often fail to expectations of enterprise-level grade security in the cloud. That’s why supplementary third-party organizations are required to protect against targeted attacks and data breaches in the cloud environment.
Moreover, there is a myth about cloud computing and servers, that it’s less secure than traditional approaches. However, a 2018 study by Alert’s Logic Cloud Security discovered that on-premise storage users suffer more cyberattack events than those in a service provider environment.
Top Cybersecurity Attacks you should be aware of!
Internet of Things
The Internet of Things or short “IoT” is connecting billions of devices over the Internet to share data with each other. They are embedded with sensors and other software. IoT has made our lives much easier, for instance, we can turn off the light or switch on the air conditioner at home sitting far away from the office.
Internet of Things security is the process of protecting IoT devices from vulnerabilities.
IoT is becoming bigger and bigger day by day by 2025 there will be 41.6 billion IoT devices. Since billions of devices are connected over the internet to share data with each other even if one device is hacked the entire network is at risk. So securing the Internet of things has become a major concern.
Different threats in IoT security.
MITM: MITM or man in the middle is a security breach where cyber criminals are placed between a communication system of a client and the server. This is by far the sneakiest attack by criminals. Vulnerable Wi-Fi connections and communication lines are the easiest methods to carry out this security breach.
Identity and data theft: Hackers might attack IoT devices to gain sensitive information to carry out criminal activities.
APT: Advanced persistent threats or apt occur when the attackers gain unauthorized access to a system or a network and remain undetected for a long duration of time. Mostly sponsored by nations or very large organizations.
Denial of service: A Dos attack occurs when the system receives traffic beyond the threshold to congest the server. This attack damages the reputation of an organization. Dos attackers usually attack the web servers of very large organizations such as media companies, government companies, and banking sectors.
Summing up the list of types of cybersecurity
And that brings us to the end of our article. Do you agree with our list of types of cybersecurity niches, or do you want to include something more in the list? Feel free to comment below. If you’re a cybersecurity enthusiast, we keep adding great valuable reads, that may interest you in the longer run. We also have two level-based cybersecurity programs, where you can learn how to monitor systems and alleviate threats when they happen. Through these courses, you can become proficient in Offensive Security, Cloud Security Architecture, Security Systems Architecture, Security Teams Management, etc. Get on – hands tutorials with exclusive case studies and exciting quizzes.






















![How to Become a Security Architect: A Beginner's Guide [2025] 5 security architect](https://www.guvi.in/blog/wp-content/uploads/2025/05/How-to-Become-a-Systems-Engineer_-Expert-Guide-for-Beginners.png)





Did you enjoy this article?