Gain powerful cybersecurity skills and become an indispensable resource for top IT and product companies with four global certifications in ethical hacking, dark web, and other cybersecurity domains. 100% results. Top-class upskilling.
Enroll Now & Get Flat 80% OFF!
₹9999 ₹1999/-
Gain powerful cybersecurity skills and become an indispensable resource for top IT and product companies with four global certifications in ethical hacking, dark web, and other cybersecurity domains. 100% results. Top-class upskilling.
Enroll Now & Get Flat 80% OFF!
₹9999 ₹899/-
Gain powerful cybersecurity skills and become an indispensable resource for top IT and product companies with four global certifications in ethical hacking, dark web, and other cybersecurity domains. 100% results. Top-class upskilling.
With 7 days refund policy*
Capture one of the ripest job markets in this dry placement season by acing trending ai skills through Cybersecurity Bundle!
50K+
Job Openings by 2024 (Top 5 trending technology)
₹12 LPA
Average salary of Cybersecurity Professional in India (Glassdoor)
31.3%
The global Cybersecurity market 2020 to 2023(Payscale)
Transform into an advanced cybersecurity professional from a beginner. Learn from a curated selection of self-paced, upskilling courses with detailed modules offering expert guidance.
Learn from scratch, make a career switch, or simply upgrade your skills, this course is everything you need if you’re a
We are most trusted vernacular ed-tech company delivering world-class learning experiences by providing highly effective & finest learning solutions, breaking the language barrier in tech learning for more than 2 million learners worldwide.
"You will be lucky to find quality courses on GUVI. I must say that I was really lucky to get courses at such a low and discounted price. I got more than 9 hours of video and around 20 more resources to gain knowledge of programming. GUVI provides a wide variety of courses both technical and non-technical. I suggest GUVI is the best choice."
"What makes GUVI different is that it provides vernacular courses which make it easy to understand & practice platforms like CodeKata & WebKata, all these helped me improve my practical programming skills in the front end, back end. I highly recommend it if you want to get started with something new."
"I have opted for a combo-course that starts with the basics of the popular technologies and made me a pro in its domain... Codekata is very damn helpful to crack placements because it improved my efficiency in coding... we just need to be persistent and that’s all it takes. I am very happy to encounter GUVI!"
"You will be lucky to find quality courses on GUVI. I must say that I was really lucky to get courses at such a low and discounted price. I got more than 9 hours of video and around 20 more resources to gain knowledge of programming. GUVI provides a wide variety of courses both technical and non-technical. I suggest GUVI is the best choice."
"What makes GUVI different is that it provides vernacular courses which make it easy to understand & practice platforms like CodeKata & WebKata, all these helped me improve my practical programming skills in the front end, back end. I highly recommend it if you want to get started with something new."
"I have opted for a combo-course that starts with the basics of the popular technologies and made me a pro in its domain... Codekata is very damn helpful to crack placements because it improved my efficiency in coding... we just need to be persistent and that’s all it takes. I am very happy to encounter GUVI!"
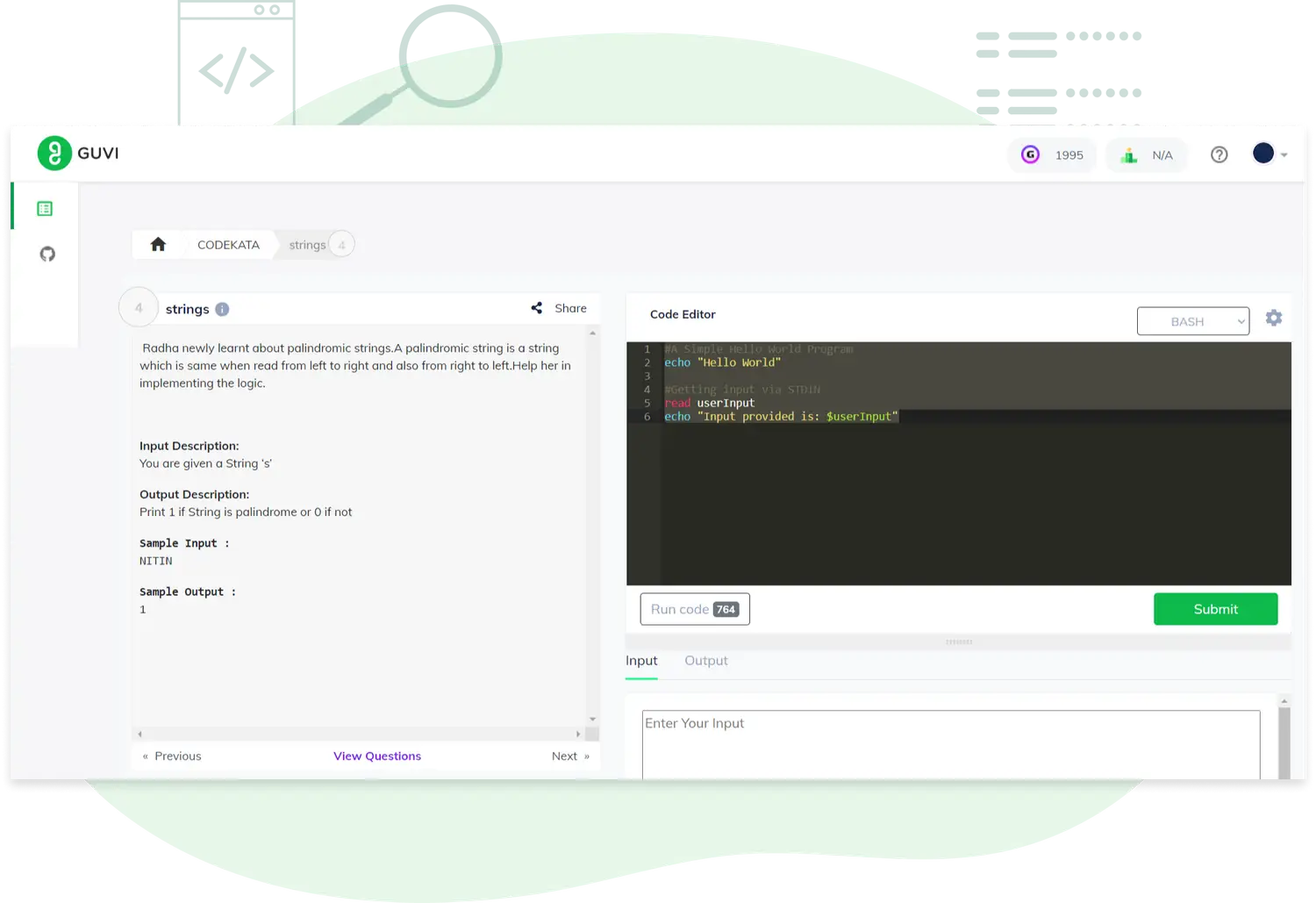
A tool-kit specifically developed to boost the coding skills and makes you ever-ready to crack interviews.
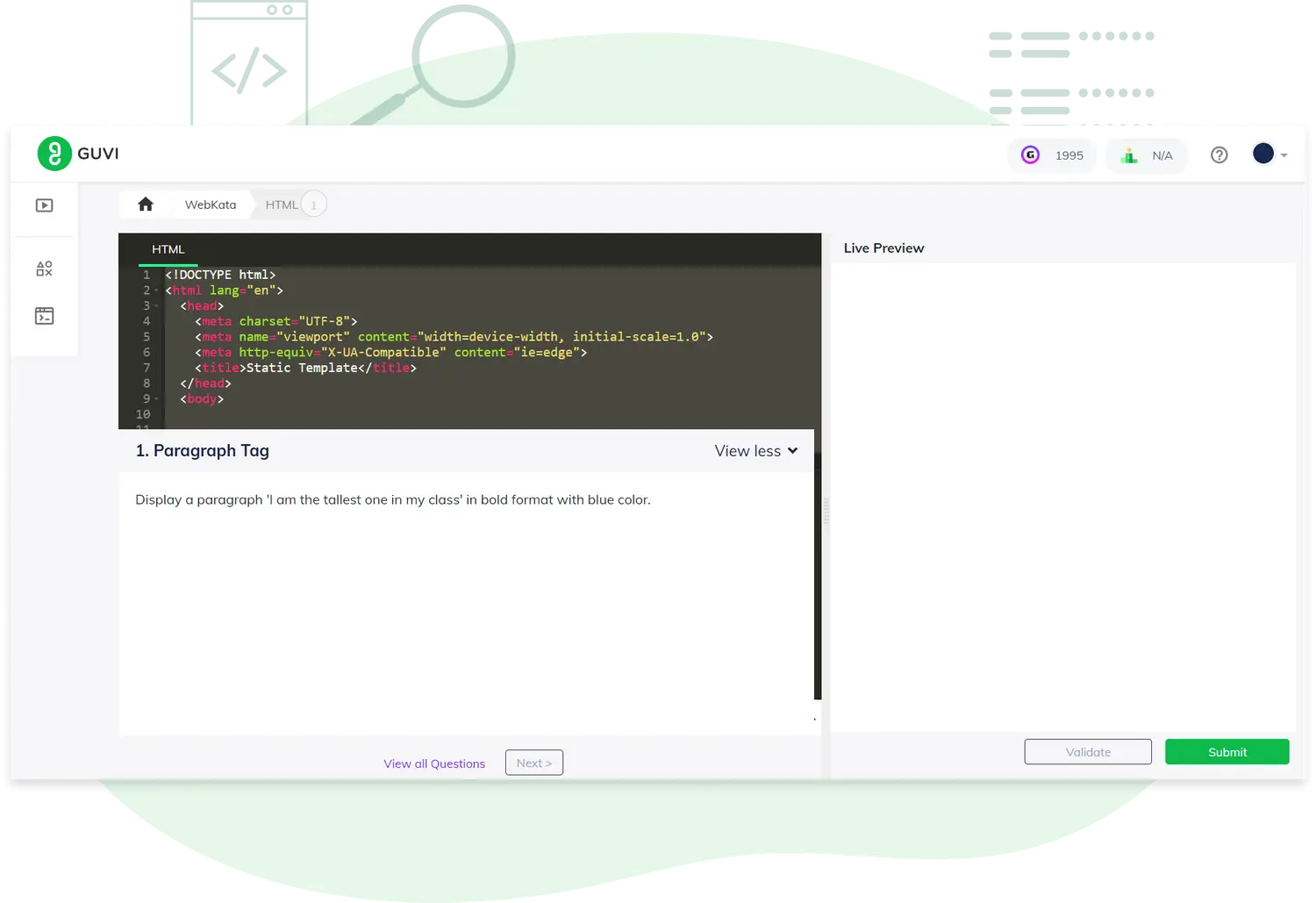
A cloud-based module to hone your front end skills without any hassle of local environment setup.
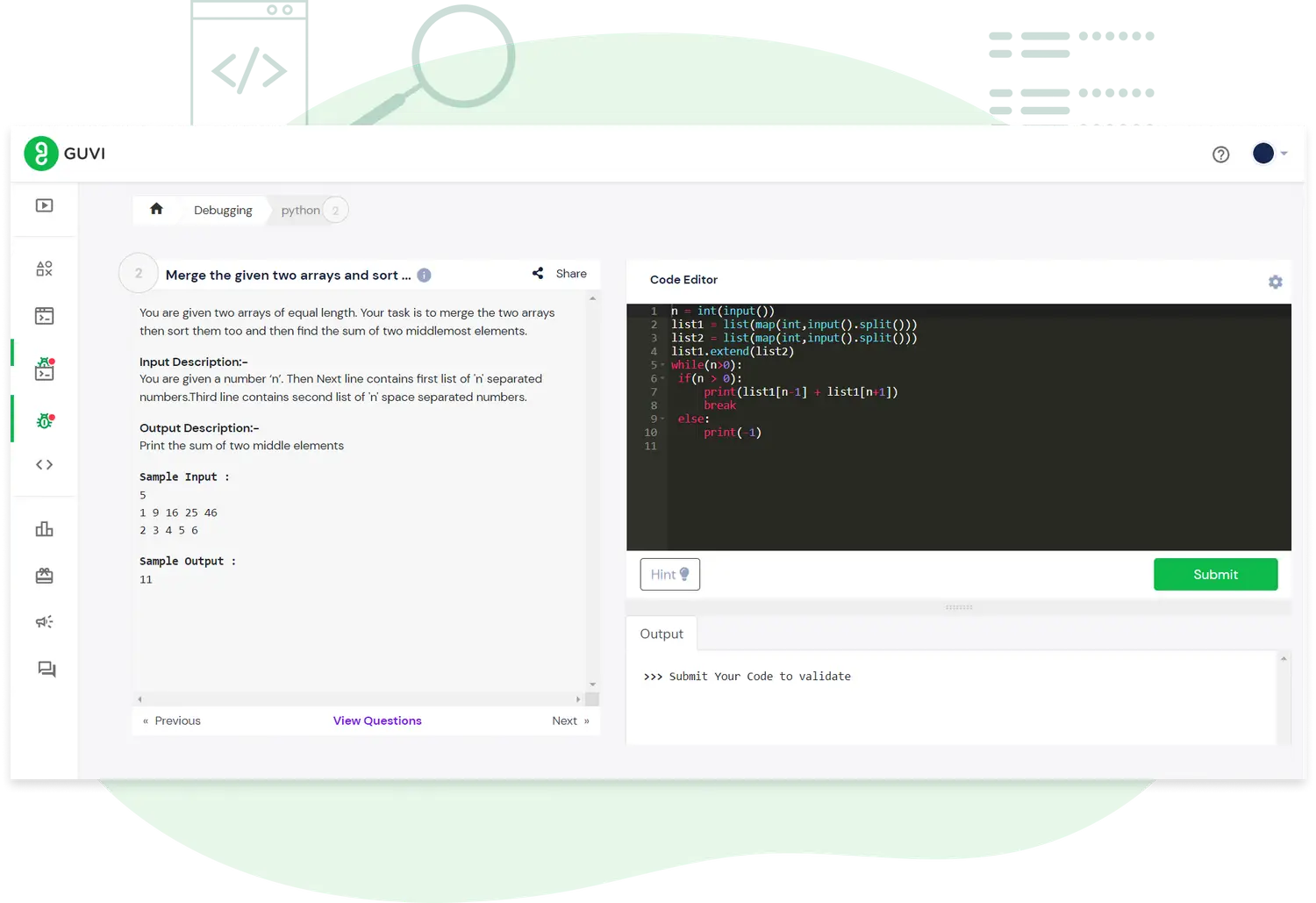
Practising on Debugging will help you get started and be familiarised with programming.
GUVI IDE is an Integrated Development Environment that lets you write, edit, run, test & debug your code.
Buy 4 courses @ ₹899 only
With 7 days refund policy*
With 7 days refund policy*